Published January 8, 2025
Every morning I get up and check what malicious packages my detector had found the night before. It’s like someone checking their fishing nets to see what fish they caught.
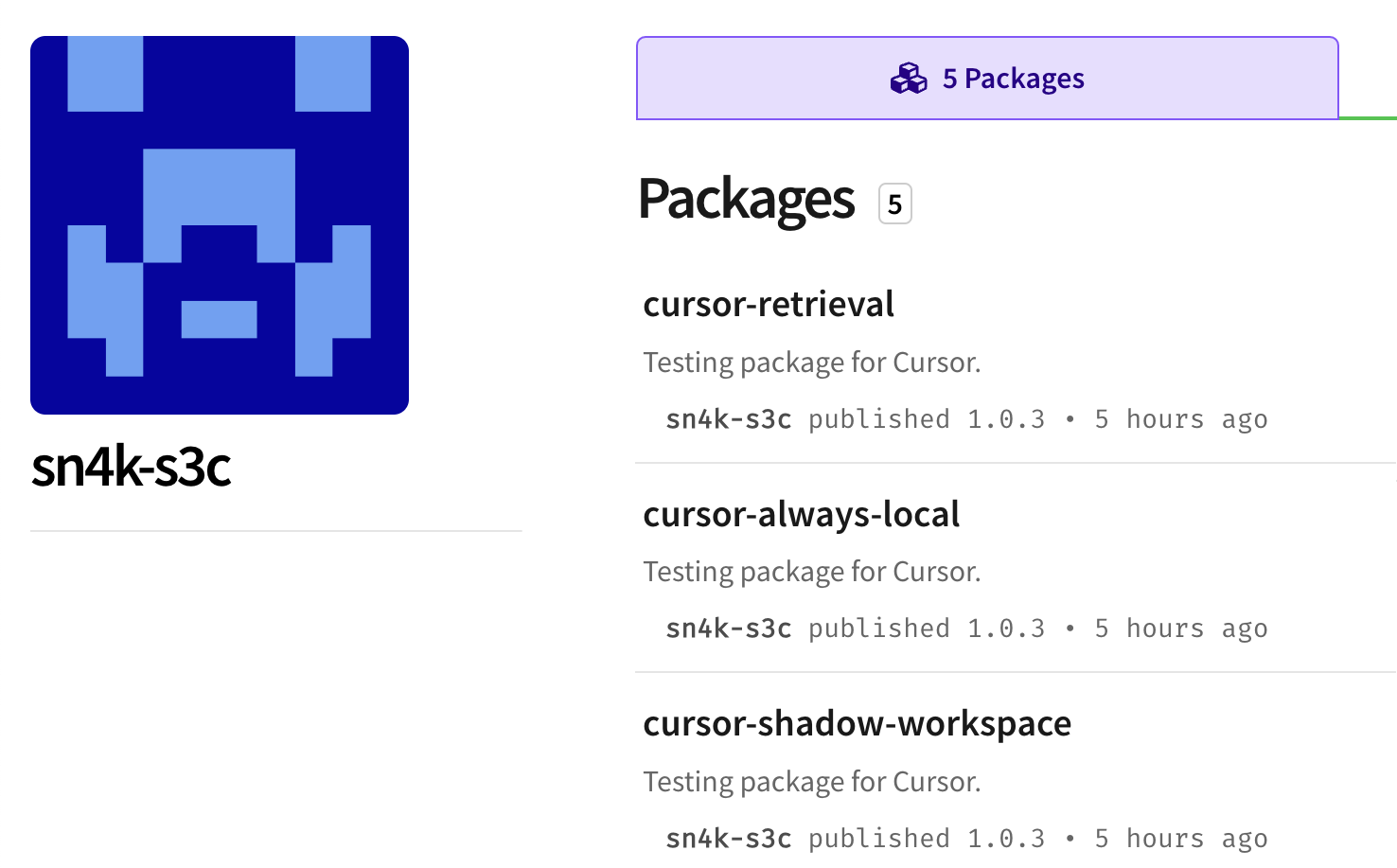
As I was looking at last nights malicious packages I noticed something strange: Someone from Snyk had deployed several packages to NPM. Even weirder, the names of those packages appeared to show they were targeting Cursor, the hot new AI coding company.
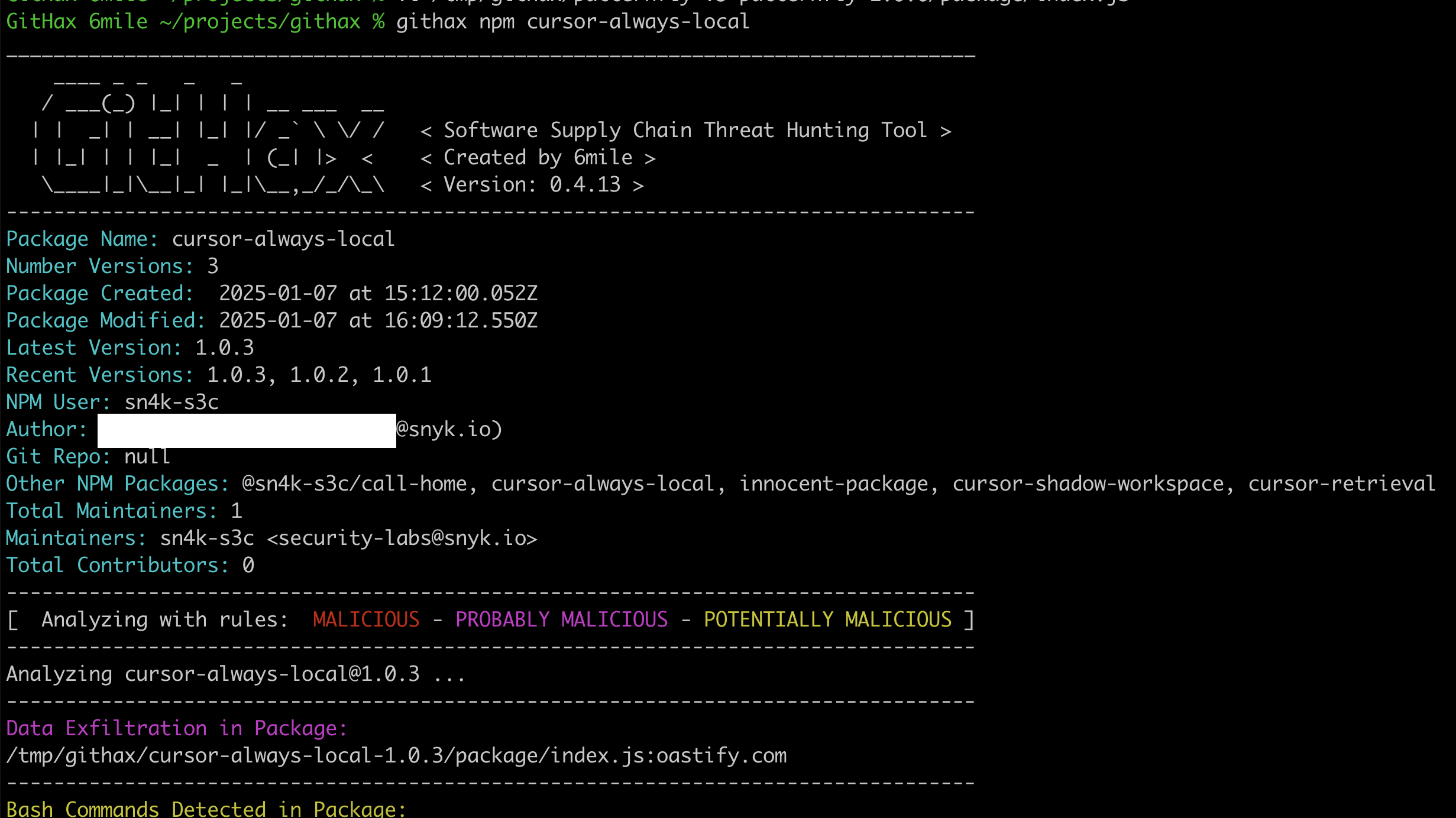
These packages were deployed by an NPM user named sn4k-s3c. The packages are named things like “cursor-retreival”, “cursor-always-local” and “cursor-shadow-workspace”.
If you install any of these packages they will collect data about your system and send it to an attacker controlled web service.
You can find the packages on NPM here: https://www.npmjs.com/~sn4k-s3c
You can see in this screen shot that the package is grabbing the output of a env command which will include many configuration options for your system. Often things like AWS keys, NPM tokens, GitHub credentials and other sensitive variables are exposed by the env command, so guess what? The threat actor now has all those credentials too!
You can see in the screenshot that the data is then exfiltrated to a website that the attacker owns.
Now, typically, when we see packages like this, they are attempting to perform a dependency confusion attack on a specific company. I don’t know if Cursor.com has a bug bounty program or a specific background. Still, I would suspect that Cursor has several NPM private packages named “cursor-always-local”, “cursor-retrieval”, and “cursor-shadow-workspace”. The person who created these packages is probably hoping that Cursor employees accidentally install these public packages, which will send their data to the attacker-controlled web service.
Luckily, in addition to me seeing these files, the OpenSSF package analysis scanner identified these packages as malicious. OSV generated 3 malware advisories: MAL-2025-27, MAL-2025-28 and MAL-2025-29. You can see the malware advisories here: https://osv.dev/list?q=cursor&ecosystem=npm
Who deployed these malicious packages?
Okay, we know what the packages do when installing them, and we think they target Cursor.com. Who would do this? Well, the answer is in the NPM package metadata.
The user who published the NPM package uses a snyk.io email address for the Snyk Security Labs team. This part of the metadata cannot be faked. The author field in the metadata specifically mentions an employee at Snyk. This part of the NPM package metadata can be faked, but since the publisher is a verified Snyk email, my guess is that this genuinely came from Snyk.
What can you do?
I’ve alerted NPM but these packages haven’t been marked as malicious yet, so no security tool could protect you from these malicious packages. Unfortunately, that’s how most software supply chain security tools work: you have to know that a package is malicious before the tool can protect you.
But in general, it’s a good idea not to install NPM packages blindly. If you know what to look for, there are definite signals that these packages are dodgy. All of these packages have just two files: package.json and index.js (or main.js). This is one of several flags that you can use to determine if a package is legit or not.
Hopefully, NPM will remove these packages soon.
UPDATES!
JANUARY 15, 2025
The Snyk researcher took the cursor packages offline the day after this blog post went public.
Then, on January 14, The Register ran this article: https://www.theregister.com/2025/01/14/snyk_npm_deployment_removed/
Then, the same day Snyk posted a response on its blog effectively arguing they had done nothing wrong: https://snyk.io/blog/snyk-security-labs-testing-update-cursor-com-ai-code-editor/