Our research has identified a package masquerading as the popular NPM package “Prettier” library. This package was published in the NPM registry in September 2024 and was taken offline in mid January 2025.
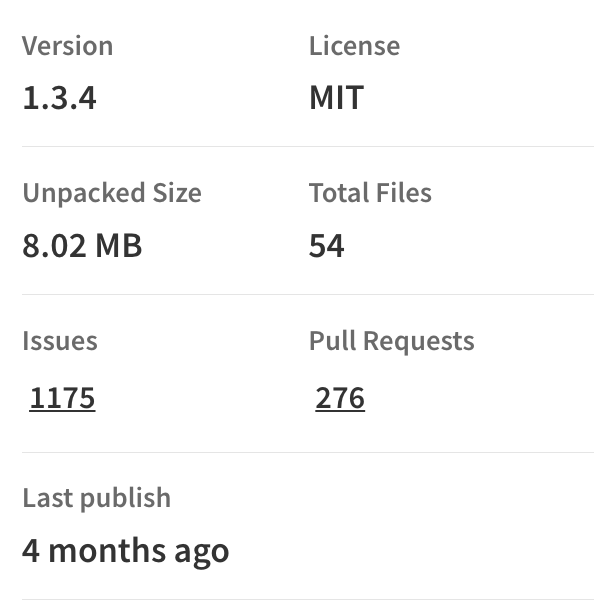
The package was published by a user named “kamations” 4 months ago and and targets developers who use Microsoft Windows to drop malware. The prettier-s package has been hiding in NPM since September using a cleaver trick to hide its malicious payload.
TIP: Scroll to the bottom for IOCs
What is Prettier?
Prettier is a popular Javascript library that formats source code or config files in a specific, standardized way.
Prettier is a legitimate, popular and actively maintained Javascript library that was originally published 8 years ago. Its NPM package is named simply “prettier”, and you can find it at https://www.npmjs.com/package/prettier. The prettier NPM package is downloaded more than 40 million times a week, and almost 20,000 other NPM packages depend on Prettier to work.

Malicious actors are copying the Prettier NPM packages
Threat actors have realized that they can deploy their malicious payloads by piggybacking on the name and reputation of legitimate projects like Prettier. Lookalike names or typo-squatted names are super common, but in this case, the threat actor has simply added a ‘-s’ to the name of the package. It’s not sexy, but unfortunately, it works.
I’m including side-by-side screenshots of the two packages so you can see how similar they are. On the left, is the legitimate package “prettier” and on the right is the malicious package “prettier-s”. Obviously, the number of collaborators is different, and if you look closely, you can see that the file size and total files are the same.
I found this package when I was working on a different software supply chain attack that was targeting the marked-js ecosystem. My GitHax tool alerted that this lookalike package existed, and I took a closer look.
NPM stats can be faked
One of the biggest problems with the NPM ecosystem is that it’s easy for malicious actors to fake some of the details in their malicious package uploads. For example, in the image to the right which was taken from one of the malicious packaages, the repository and homepage list the legitimate marked-js information. It’s the same with the Issues and Pull Request statistics at the bottom. These fields are pulled from the GitHub repository you list in the package metadata, which can be anything you want to put there.
The problem with that is that NPM doesn’t verify that you own the GitHub repository, so what threat actors do is include a legitimate GitHub repo in their malicious package metadata to “piggyback” off the reputation of the original, legitimate GitHub repo.
This helps their malicious package appear more legitimate and is a common technique that malicious actors use to hide in plain sight.
Watching the attack evolve
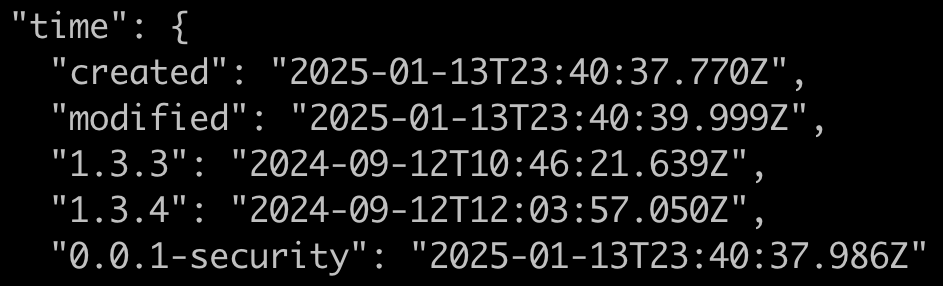
This package was originally published to NPM September 12, 2024 and quietly hid undetected or months because of a neat naming trick.
Unicode naming trick
This prettier-s package hides a malicious binary file targeting Microsoft Windows systems. How it pulled this off is pretty slick. The malicious payload is a binary file named ‘20240909142451_b6fdff38e7864af9a35357ef430ce5edgpj.exe’. But if you look closer, that filename actually has unicode characters embedded in it.
You can see that more clearly in the image below where I force the unicode to become visible:
The intent of this naming trick is to evade security scanners that talk to the NPM API or scrape the NPM website.
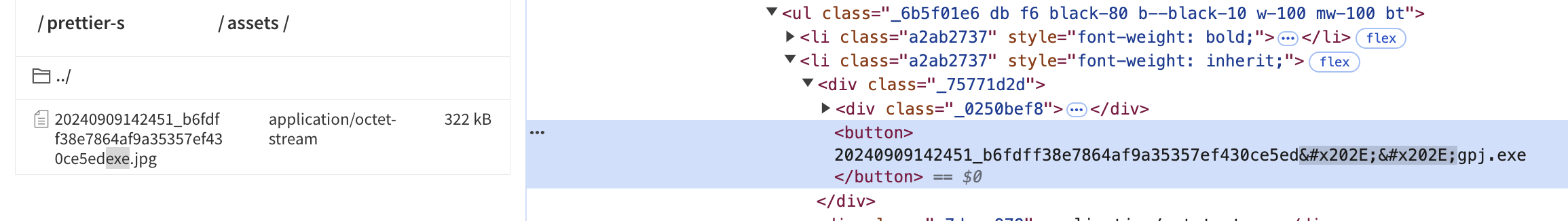
To make this is little more obvious, I’ve browsed to the prettier-s npm package at https://www.npmjs.com/package/prettier-s and opened up the file explorer in the npm site. I’ve then highlighted the filename and opened devtools on the right so you can see the actual filename.
If you look closely on the left you can see that the filename ends with exe.jpg which makes this look like an image file ending in .jpg. My suspicion is that the author of this package, Kamations, was trying to hide their binary as a jpg image file.
How well this worked to hide the file is unknown, because when I tested this by making a call to the NPM API, the filename looks correct to me.
What does the malware do?
Virustotal has confirmed that marked.exe is malicious, but what does it do? To find that out, let’s run the file in a sandbox. I’ll use the Any.Run sandbox, but there are others like Joe’s sandbox and Recorded Futures Triage.
When I execute the marked.exe file in Any.run, the sandbox watches what it does, what it downloads, and what IP addresses or domains it talks to.
Will source code or package scanning tools protect you from these malicious packages?
Okay, so we’ve verified that this package is malicious. Even worse, it drops active malware onto any hosts that install the NPM packages. That sounds like something that security scanning tools should pick up, right?
Well, guess what? Software composition analysis (SCA) tools are not very good at identifying known malicious packages. So even if GitHub Security Advisory or OpenSSF’s OSV mark the package as malicious SCA tools, they typically don’t report this fact to paying customers.
Indicators of Compromise (IOCs)
Based on my research this package has several IOCs that your team can hunt for:
Files:
20240909142451_b6fdff38e7864af9a35357ef430ce5edgpj.exe – sha256 hash: b7e07bcff88f9c6b8391a3dcb69584bfaf81bfdb5166f27c2466d786c3fc16d6
NPM Packages:
prettier-s, marked-cs, marked-ps
What can you do?
I’ve alerted NPM and the package has been removed from the NPM registry. However, no security tools marked this package as malicious until NPM removed it. Unfortunately, that’s how most software supply chain security tools work: you have to know that a package is malicious before the tool can protect you. And most of the tools out there are not able to identify malicious packages themselves.
But back to what you can do: Generally, it’s a good idea not to blindly install NPM packages. If you know what to look for, there are definite signals that these packages are dodgy. All of these packages have just two files: package.json and index.js (or main.js). This is one of several flags you can use to determine whether a package is legit.