A new software supply chain attack is affecting GitHub users. The new threat, “Gitloker” targets GitHub users repositories with a simple but effective attack: deleting everything they have access to and then attempting to extract ransom payments.
DISCLAIMER: This attack is still unfolding, and this report will be updated as new information becomes available. We will explicitly mention anything we suspect to be true but haven’t yet confirmed.
Let’s dive right in and see how this attack works
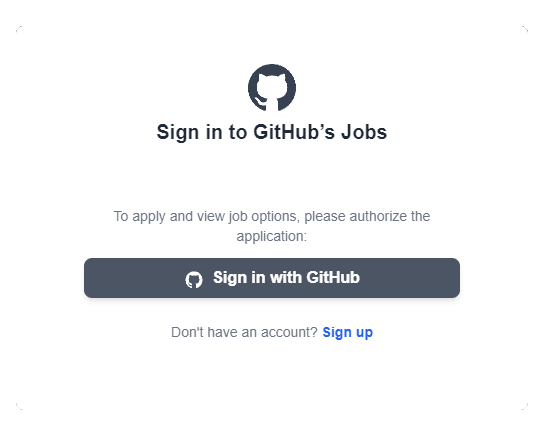
Victims are targeted via phishing emails or GitHub job postings. If a developer clicks on the job post, they are redirected to a GitHub lookalike domain such as “auth.githubtalentcommunity[.]online” or “githubtalentcommunity.githubcareers[.]online” and prompted to log in.
Unfortunately, the website the user is directed to is a fake GitHub authentication page.
Once the victim provides their login details, the threat actor gains access to their GitHub account, deletes everything, and then replaces the deleted repositories with a ransomware-like message.
Here’s a technical breakdown of the attack:
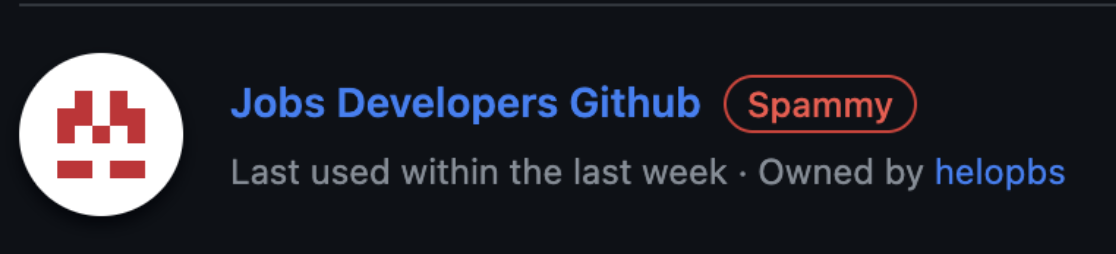
When the victim clicks on the fake auth page, it appears to install a malicious GitHub application called “Job Developers Github”.
This malicious GitHub application gives the attacker the permissions they need to write and delete repositories, but also to manage the GitHub Organization which is how most of the damage from Gitloker is being done.
The victims unfortunately are clicking on a permissions request from GitHub that allows the attacker to take over and compromise the account and Organizations.
This is not meant to blame the victim, and should rather speak to how little attention is given to these permissions requests from SCM and cloud providers. Also, this is a good time to point out that this attack isn’t a vulnerability or zero day in GitHub. Instead, this attack takes advantage of developers’ trust and their elevated privileges.
We initially found out about this attack when the Chilean security researcher Germán Fernández’s tweeted about it: https://x.com/1ZRR4H/status/1798412587484496068
German’s analysis was great, but SourceCodeRED researchers decided to go deeper to see if we could learn more about the attack. If we were lucky, maybe we could identify the attacker and/or find TTPs involved in the attack that organizations could use to their benefit.
So, with that in mind we started researching the problem by searching GitHub repositories and commits for the term “gitloker”.
We found quite a few affected GitHub users and reached out to several while conducting our analysis.
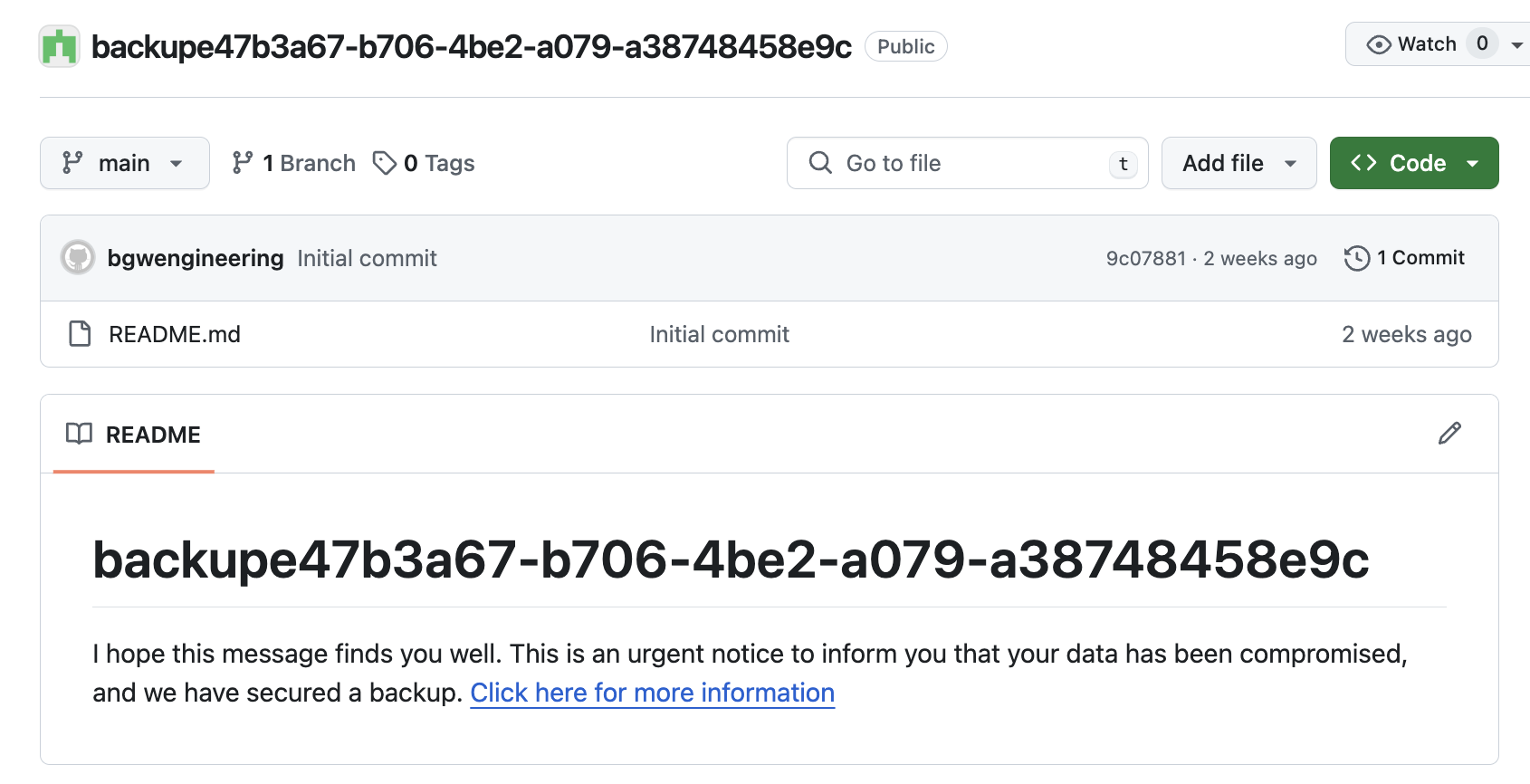
After a GitHub user has been compromised, this is what is left behind. A repository with a README markdown file named “backup” and then some randomly generated characters.
After deleting all the repositories the GitHub user has access to, the attacker leaves a message in that README that says:
“I hope this message finds you well. This is an urgent notice to inform you that your data has been compromised, and we have secured a backup”
The attacker goes on to say that the victim should contact them on Telegram.
The attacker uses a GitHub user named “taehyunseungminatae”, which we believe to be a “code puppet”—a fake persona created by threat actors to interact with other people or resources on GitHub.
Interestingly enough, this name “taehyunseungminatae” is used several times by the attacker across multiple platforms.
The original posts from German and people responding to his tweets suggest that only Brazilian developers were targeted. Our research shows that about half the victims are in Brazil, but the other half include targets in the US, Hong Kong, Russia, Indonesia, India, and the UK.
In addition to the Brazilian developers, the real target of this attack were companies that the compromised developers were working for. Some of the victims include a shipping company, software development agencies, charitable organizations, a crypto company, a computer gaming company and a legal firm.
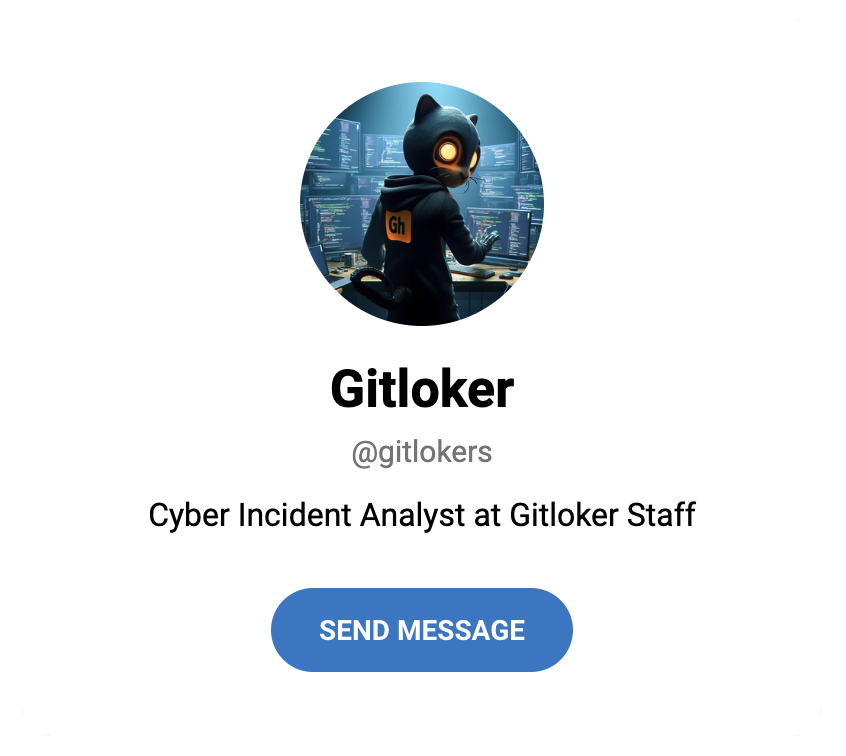
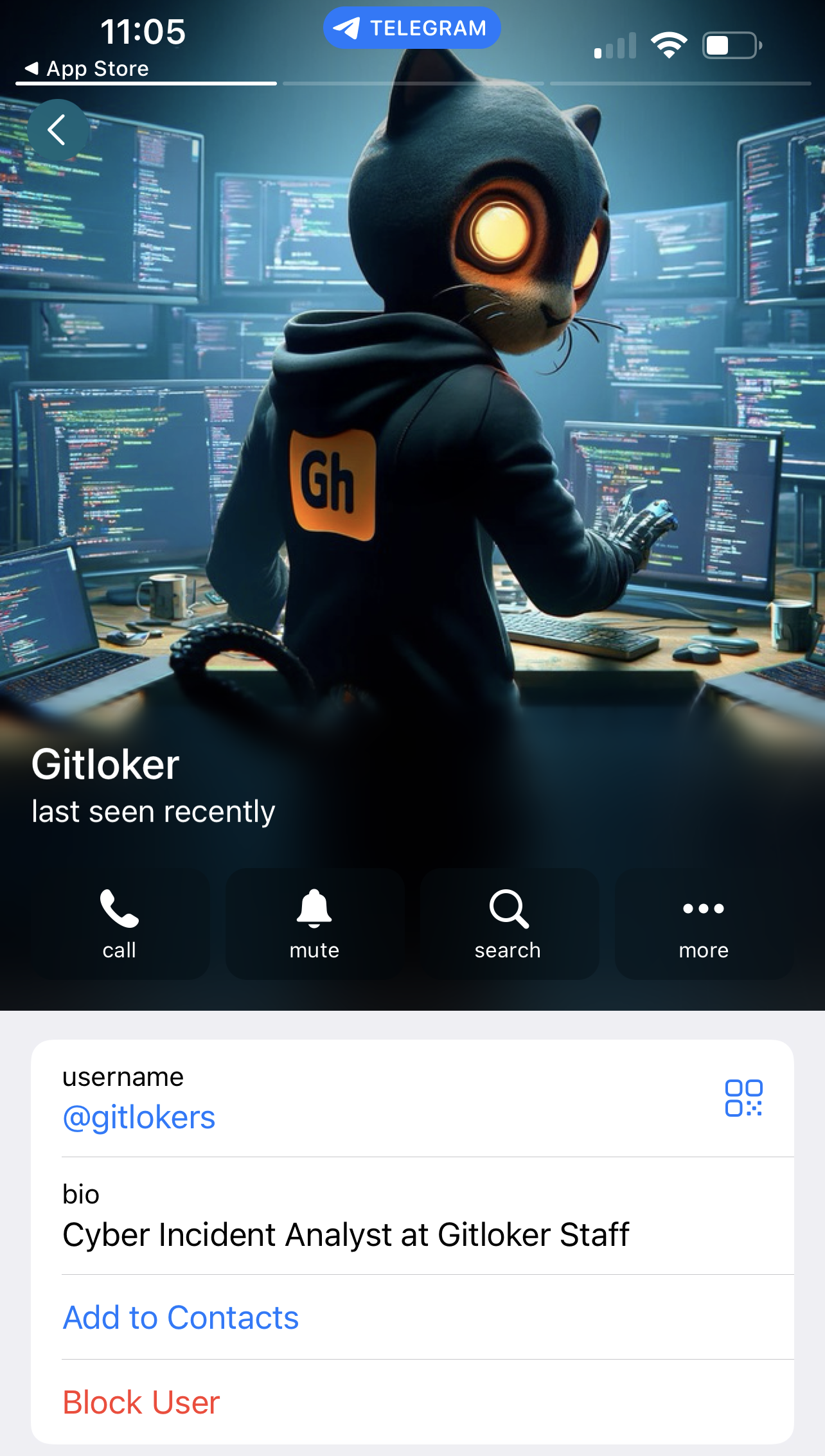
The attacker’s message in the GitHub repository directs victims to a Telegram user named @gitlokers. The @gitlokers user on Telegram has crafted a custom “hackercat” logo for their attack.
The attacker lists their employment as “Cyber Incident Analyst at Gitloker Staff.” This could be part of their ploy to appear as cybersecurity analysts.
If you look at the profile for the @Gitlokers user on Telegram, they appear to have crafted a custom “hackercat” logo for their attack.
We have to admit that it’s not bad. Especially, for a AI generated image.
The attacker also lists their employment as “Cyber Incident Analyst at Gitloker Staff. We don’t know if this is part of their ploy. Maybe they want to pretend like they are actually cybersecurity analysts who want to help? It wouldn’t be the first time attackers pretended to be the good guys coming to the rescue.
How is this a software supply chain attack?
This attack initially looked like a limited wiper-style attack on several dozen GitHub users. However, upon closer inspection, we recognized the signs of a software supply chain attack.
A supply chain attack is a cyberattack that targets a trusted third-party vendor providing vital services or software to the supply chain. Can you think of anything more vital to a software company than its developers?
Developers are part of the software supply chain
Malicious actors target software engineers as they know these devs often have access to multiple organizations. Even better for the attacker, these devs typically have elevated privileges. For example, many developers own the GitHub Organization for a company.
In the case of the Gitloker attack, when a developer was compromised, the threat actor used their access to attack multiple organizations simultaneously.
The compromised developer was the shared component in the supply chain for these companies’ software. SourceCodeRED has identified multiple examples of a single GitHub user being compromised to delete multiple GitHub Organizations.
In the example below, when a single software engineer named “danirolopes” was compromised, the attacker used the danirolopes account access to delete at least 5 companies GitHub Organizations that daniro had access to. This means that at least 5 companies lost their source code, deployment workflows, and intellectual property through one targeted software supply chain attack.
Wait, this is a ransomware attack too?
As we said earlier, initially, this attack looked like a simple wiper-style attack with limited reach. But why would the attacker go to all the trouble of doing all this, just to delete files? If the attacker is deleting everything, what’s their motive? Are they just trying to be destructive?
Well, it turns out that this is a ransomware tactic. The attacker is asking victims to send them $1000 US to get their files back.
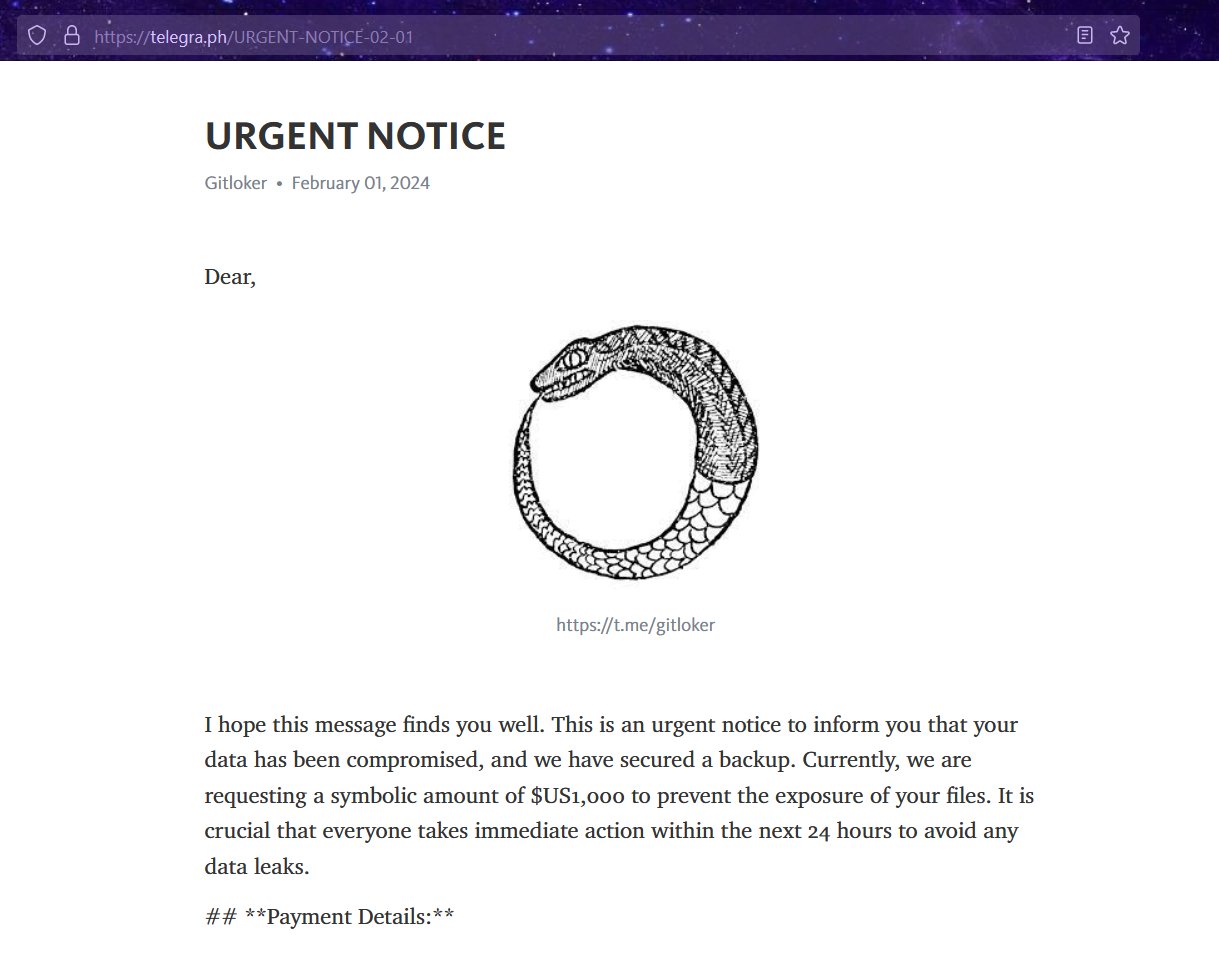
The attacker uses a website to tell his victims how to pay for their files back:
https://telegra[.]ph/URGENT-NOTICE-02-01
The website includes a longer message:
“I hope this message finds you well. This is an urgent notice to inform you that your data has been compromised, and we have secured a backup. Currently, we are requesting a symbolic amount of $US1,000 to prevent the exposure of your files. It is crucial that everyone takes immediate action within the next 24 hours to avoid any data leaks.”
This ransom message was accompanied by a specific image of a snake eating its own tail. This snake image is known as an “ouroboros”.
The final blow…
If deleting all the repositories owned by the compromised user and finding all GitHub accounts the user has access to and deleting everything, wasn’t enough, there’s one final cruel twist of the knife: The Gitloker attacker deletes the compromised user’s account in it’s entirety. Bye-bye GitHub account!
SourceCodeRED analyzed the evolution of this attack. We found that in April, the attacker changed tactics and began to delete the compromised GitHub accounts after executing their attack. The original developer’s account would be used to target any organizations or companies they worked for, and their repositories would be ransomed. However, the developer’s own account was typically deleted entirely.
The “danirolopes” user we mentioned above, for example, has been deleted.
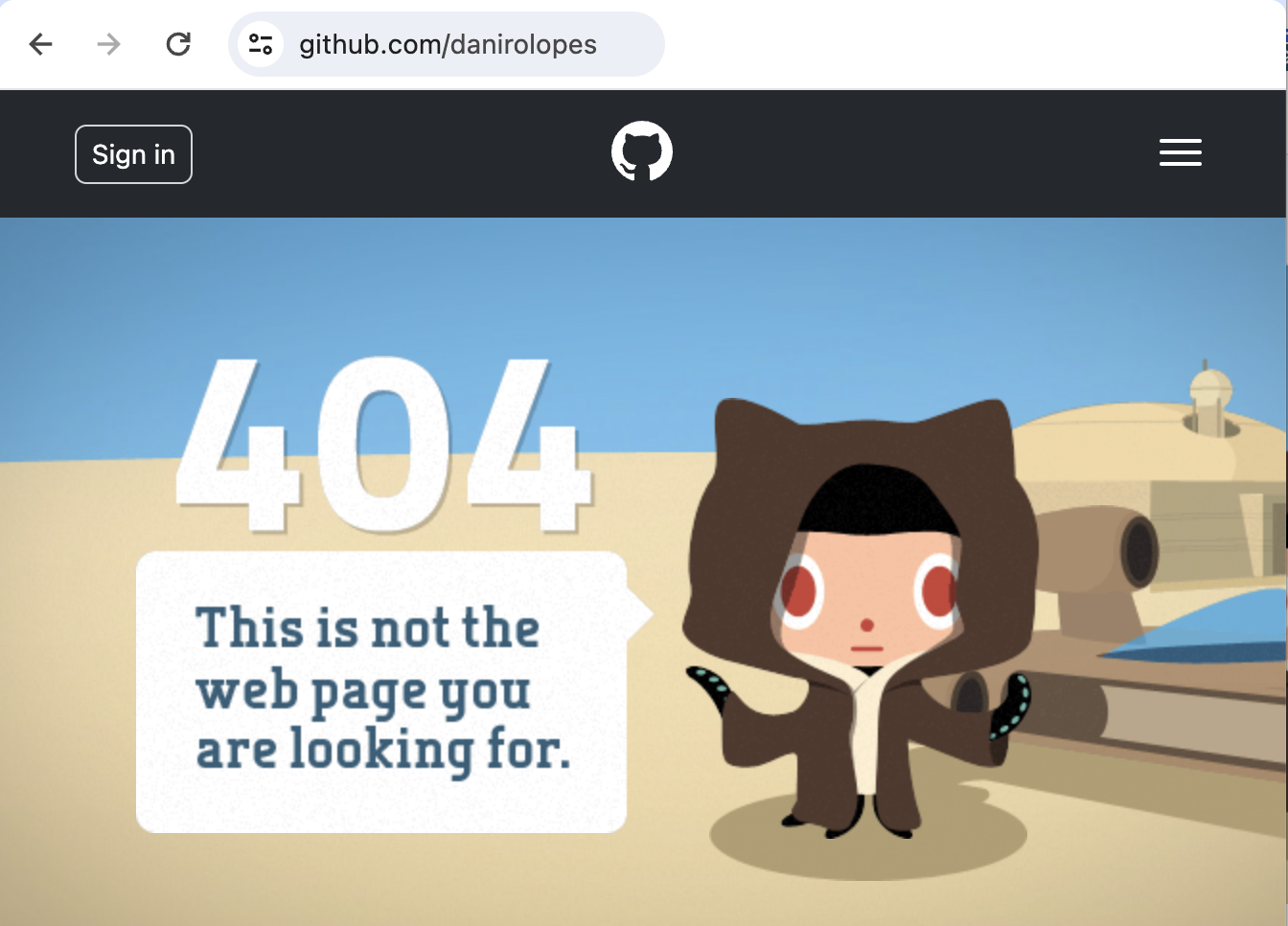
Who is the @Gitlokers threat actor?
Normally, threat actors, especially ransomware actors, are not as public as the Gitloker actor has been. The attacks themselves have happened entirely in the open: the ransomware note, the personas and GitHub users attacked are all in the public realm.
It’s a unique opportunity to use this public data to document the attack chain, and perhaps to identify who the threat actor is.
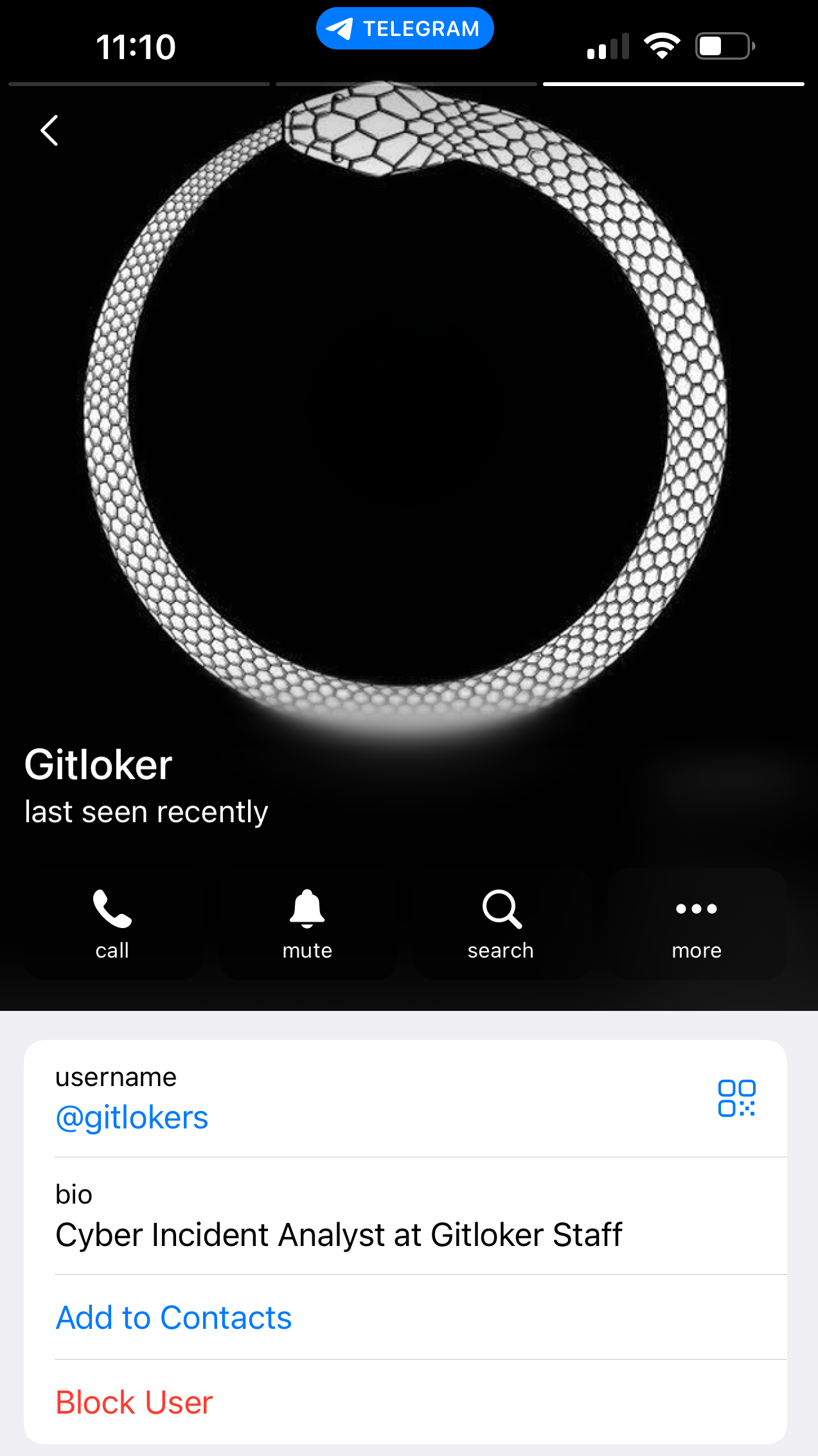
When the SourceCodeRED team analyzed the Telegram profile for @Gitlokers, we found a historical profile image of a similar ouroboros-style snake to the one we saw in the ransomware demand website https://telegra[.]ph/URGENT-NOTICE-02-01
For some reason the attacker has used this style image twice that we’ve seen.
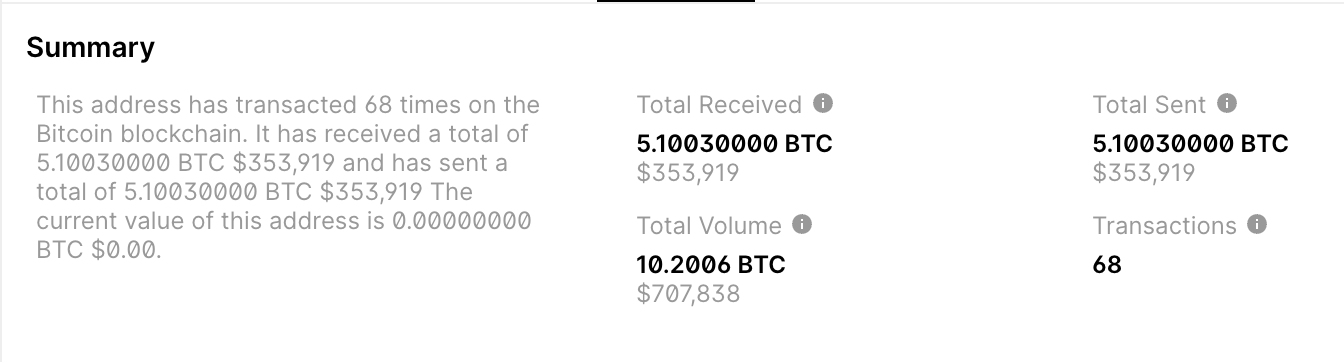
Because the Gitloker actor published the Bitcoin and Ethereum wallet addresses, this provides a unique opportunity to follow the transactions.
Ethereum wallet address: 0x00fA622555Aae36d7f277be2646Bb09548264dc9
Bitcoin wallet address: bc1ql9px8kqdq6zgkxahxv7wvk25flsqfmr9gkcz7a
There was another historical Telegram profile image that we found as well.
This image was of an Asian male. We cross-referenced this image and found several uses for the same photo on LinkedIn and several other platforms.
It’s unlikely that the attacker accidentally included a headshot with their Telegram profile, but ya never know…. Over the years we have seen some pretty bad OPSEC from new threat actors. Regardless, we have edited the profile picture out of an abundance of caution.

Additionally, the SoureCodeRED team was able to extract additional data from the Telegram profile about the attacker’s identity.
Thanks for reading to the end! Just below you will find some tips if you want to threat hunt for the Gitloker (or similar) style attacks. Additionally, you can find our contact details if you want to reach out to us.
Cheers!
Tips for Threat Hunting
- Look for GitHub Apps that have been installed recently
- Look for GitHub Apps with Read/Write permissions to ALL repositories
- Look for GitHub Apps with full admin permissions for the GitHub Organization. Basically, nothing should have this.
- Search your GitHub repositories for the terms: taehyunseungminatae, helopbs
- Audit your users in GitHub. You’ll need to check both the repository level and Organizational level as you can add users in both places.
- Make sure that MFA is enabled in GitHub for all developers, collaborators, and maintainers. GitHub has some great options for MFA which you can read about HERE.
- Make sure all access tokens are scoped correct and are set to expire. You can read more about token expiration HERE.